Blog
OUR REGULARLY UPDATED EDUCATIONAL RESOURCES.

Tips for Setting Good Passwords
Pro tip: You don’t actually have to change your passwords if you set good ones to start with.
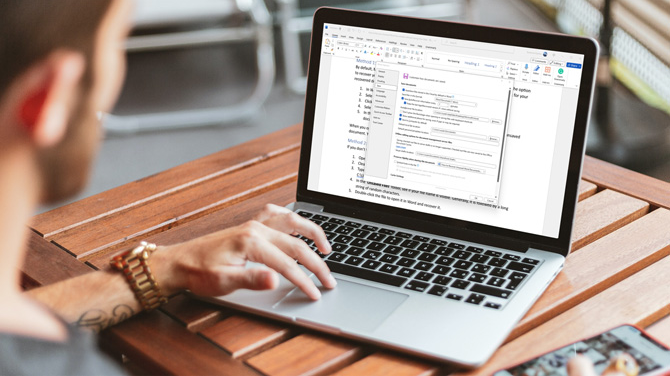
Don’t Panic! A Step-by-Step Guide to Retrieving Unsaved Word Files
Have you ever lost a Word document due to an unexpected PC crash?

Revealing the Silent SSD Killer: Death by Dust
Dust, seemingly innocuous and ever-present, can silently wreak havoc on our devices, even solid-state drives (SSDs).

3 Things You Probably Didn’t Realize Microsoft Word Can Do
Let’s delve into three of the things you probably don’t know Word can do.

Americans Have Bad Password Habits. Are You Part of the Problem?
Have you used “password,” “admin,” or “12345” for any of your accounts? You’re not alone.
Give Us A Call!
Hours
Monday - Friday
8:30 AM - 5:30 PM (EST)
Emergency Hours
Sunday - Saturday
8:30 AM - 8:30 PM (EST)
Contact
Phone
(732) 780-8615
Emails
Corporate Office
91 Sandalwood Drive, Marlboro, NJ 07746
Accounting and Technical Support Office
14 Mundy Road, East Brunswick, NJ 08816
