
by Stephen Gross | Aug 6, 2019 | Mobile Computing, Tech Tips for Business Owners
Google is way more powerful than most people realize. Regular searches are helpful, but they don’t even scratch the surface of Google’s abilities. Sometimes, your basic search inquiries may not be enough or you need a tip to get the best results. There is...
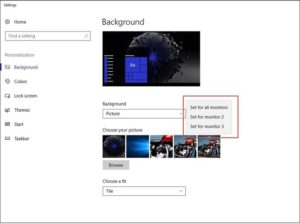
by Stephen Gross | Jul 25, 2019 | Tech Tips for Business Owners
Downloads(click link to download PDF): 2019 October – Cybersecurity Awareness Month Worst Year Ever! 2019 October – 5 Tips for Cybersecurity Awareness Month 2019 August – MS Word Hidden Tricks – Part 2 2019 July – 5 MS Word Hidden Tricks...

by Stephen Gross | Jul 10, 2019 | Tech Tips for Business Owners
By Anthony Farina Have you ever noticed those F keys in the top row of your keyboard? Did you know that they can do some useful things? I’ll be explaining what some of the most useful features of these buttons are so that you can use your computer more efficiently! F1...

by Stephen Gross | Jul 9, 2019 | Tech Tips for Business Owners
By Zachary Longo As the number of internet users continues to rise, so does the probability of hackers entering one’s computer to take advantage of their personal information. In today’s world of information technology, anti-virus software has become the...

by Stephen Gross | Jul 9, 2019 | E-mail, Mobile Computing, Tech Tips for Business Owners
By Jonathan Heitz What is Firefox Send? Firefox send is a new service from Mozilla that allows anyone to share files with the click of a button. You can share files up to 1GB in size if you decide not to sign in to a Mozilla account. If you sign in, you can send files...

by Stephen Gross | Jul 9, 2019 | Tech Tips for Business Owners
Do you ever feel like there should be a faster way to navigate on your computer? Maybe you’re trying to find a certain word in a webpage, but it takes forever to skim through the whole thing. Or maybe you want to switch between tabs on your internet browser without...







