
Last month we went over four types of spam emails you may find in your mailbox. Here are an additional four you should be on the lookout for.
1. Nearly Blank Emails
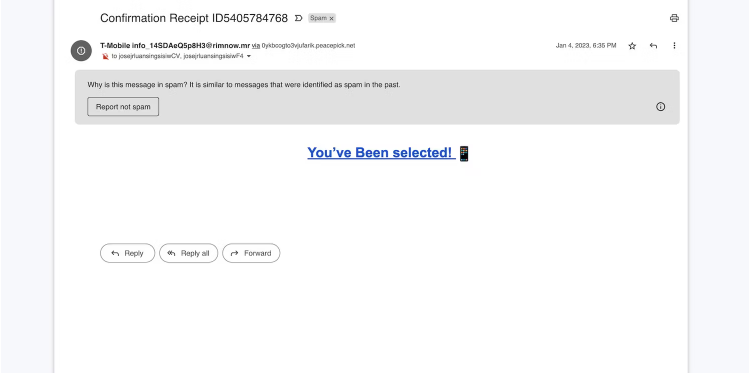
While many spam emails trick victims with complex, made-up threats and rewards, others use short one-liners. They often contain nothing but links. The anchor text will likely use weird, open-ended statements to pique your curiosity and encourage you to visit their page.
Avoid interacting with these messages. Remember that legit emails always have a greeting, body, and closing. No respectable brand sends spam emails with vague content, random links, and shady promises.
But if you’re still unsure, analyze the page’s contents. Copy-paste the phishing link on a separate document and analyze the address. It should show the source website.
2. Fake App Transaction Verifications
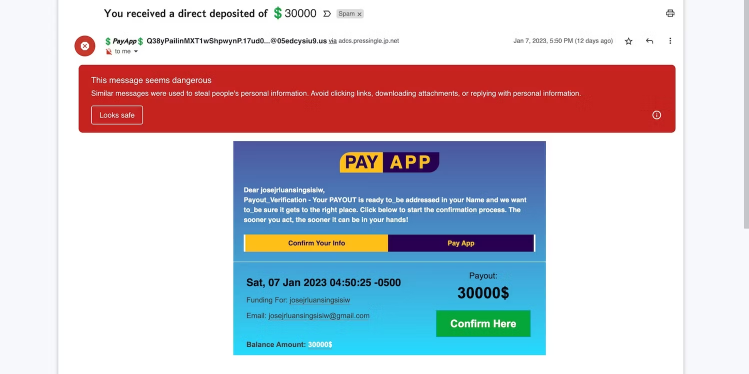
Millions of consumers prefer to use digital wallets nowadays. Although they offer convenience and security over cash transactions, they can expose you to cyberattacks, notably financial identity theft.
The biggest red flag in the above example is that it failed to copy PayApp protocols. The messages use a different color scheme; sizable transactions require more than just login credentials; and no wallet randomly sends $30,000 payout notifications.
Don’t be too quick to trust other emails from your preferred online payment companies. Criminals can also pose as them. They’ll earn your trust by duplicating logos and prompt templates, then trick you into divulging information through fake transactions.
3. Dummy Email Addresses
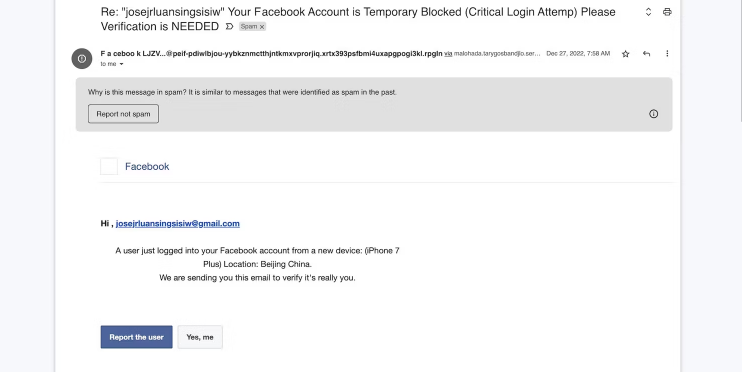
Cybercriminals gain their victims’ trust by masquerading as a widely trusted company or website. For instance, they could pose as Facebook. In the above example, you’ll see that the attacker instills fear in their recipients by duplicating account login prompts. The warning presents two actions. But considering the nature of this message, both will lead to a fake login page.
Beware of these messages; they look scarily real. Always verify the sender’s address, regardless of whether the email went to your inbox or spam folder. See if it leads to a legit source. Avoid interacting with dummy accounts that have fake domains, typos, lengthy usernames, or leetspeak (jargonistic internet abbreviations).
4. Sudden Game Invites
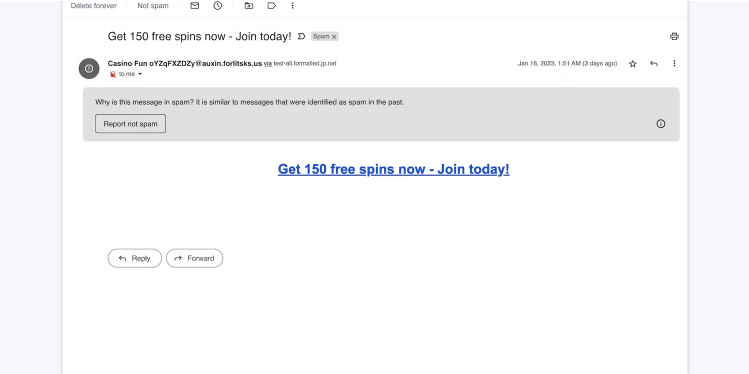
Beware of random game invites. Crooks use appealing in-game rewards (i.e. free spins or coins) to catch your attention and send phishing links. They often lead to random casino games. The “game” will say you won a cash prize before asking for your personal and banking information.
The above example looks suspicious since it’s a blank email from an unknown source. Other more sophisticated templates might try gaining your trust first by impersonating widely known gaming sites or online casinos.
The best practice would be to avoid unknown games altogether. Apart from phishing attacks, shady betting sites also steal money by withholding player funds, selling personal information, and spreading malware.
Get advanced email protection from infected attachments, suspicious links, phishing attempts, and email-based malware. Our newest service will harden your email system and put your organization in the best position to prevent potential threats. For more information contact us at [email protected] or give us a call at 732.780.8615.
Jose Luansing JR, “What Does a Spam Email Look Like?” makeuseof.com, Aug 29th, 2023
