Because employees are the core of any business, they will be the main target for cyber criminals. Making sure your people stay up-to-date with cyber security knowledge, and teaching them to recognize threats, is imperative to the security of your business. The threat landscape is constantly evolving, and so should your approach to defense.
Here are a few red flags that can help you to be guarded from a potential phishing attempt:
![]() Always double-check who the email is ‘FROM’
Always double-check who the email is ‘FROM’
- The email can appear to be from someone you communicate with, BUT the request is out of character.
- There is something “phishy” about communication from someone with whom you do not typically communicate with in your organization.
- An unexpected email from someone whom you have not recently communicated with and has attachments and/or embedded links.
![]() Check the ‘TO’ field in the email
Check the ‘TO’ field in the email
- Do you know the other recipients or are you copied in the email?
![]() Check the ‘Subject’ field
Check the ‘Subject’ field
- Is this an odd request or providing you with information that you haven’t requested?
![]() Check the email ‘Content’ carefully
Check the email ‘Content’ carefully
- Is the recipient asking you for personal information or telling you that you won something?
- False urgency! Out of the ordinary request
- A request for you to change your password
- Someone you know is in trouble and desperately needs your assistance
- Check for bad grammar and spelling errors
![]() Check ALL ‘Hyperlinks’ carefully
Check ALL ‘Hyperlinks’ carefully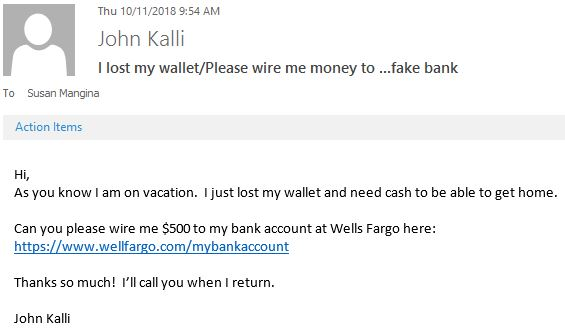
- Incorrect or misspelling in a hyperlink
email Wellfargo.com should be Wellsfargo.com
- Always hover over the hyperlink to see exactly where it leads you.
![]() Beware of Attachments
Beware of Attachments
- Beware of opening any attachments that you are not expecting.
No one wants to become a victim of a social engineering attack, so it’s important to recognize an attack in progress and not be tricked into responding to it inappropriately.
Trained and aware employees are critical to securing an organization, and an effective, ongoing internal security awareness program can help reduce your company’s vulnerability, turning the “weakest link” in your cyber defenses into its greatest strength.
One of our most important roles as a technology service provider is to protect the assets of our clients. No matter how big or small your business is, a single compromised credential could put your entire business at risk. Give us a call to further discuss how we can help in protecting your business against cybersecurity threats and how we can make technology work for your business.
Call us now at 732.780.8615 or email us at [email protected]
