 The bug, dubbed ForcedEntry, could lead to remote code execution. Apple also patches an iOS flaw that leverages maliciously crafted web content to trigger remote code execution.
The bug, dubbed ForcedEntry, could lead to remote code execution. Apple also patches an iOS flaw that leverages maliciously crafted web content to trigger remote code execution.
Time to patch your iPhones. Apple has uncovered evidence that attackers may be actively exploiting two vulnerabilities in company software to take over its devices.
The company issued the security patches today while warning the vulnerabilities could lead to remote code execution. That’s when an attacker can trigger the device to run rogue computer code, such as downloading a malicious program from the internet.
The first vulnerability, dubbed CVE-2021-30860, is particularly alarming because it can take over a device simply by sending a message to the victim, no user interaction required. In addition, the flaw affects iOS, iPadOS, macOS Catalina and BigSur, along with watchOS.
Apple is urging people to update immediately to iOS and iPadOS 14.8, macOS Big Sur 11.6, Security Update 2021-005 for macOS Catalina (and Safari 14.1.2), tvOS 14.7, and watchOS 7.6.2.
Apple credited the vulnerability’s discovery to Citizen Lab, a watchdog group at the University of Toronto, which suspects an Israeli security company called NSO Group exploited the flaw to help governments spy on targets.
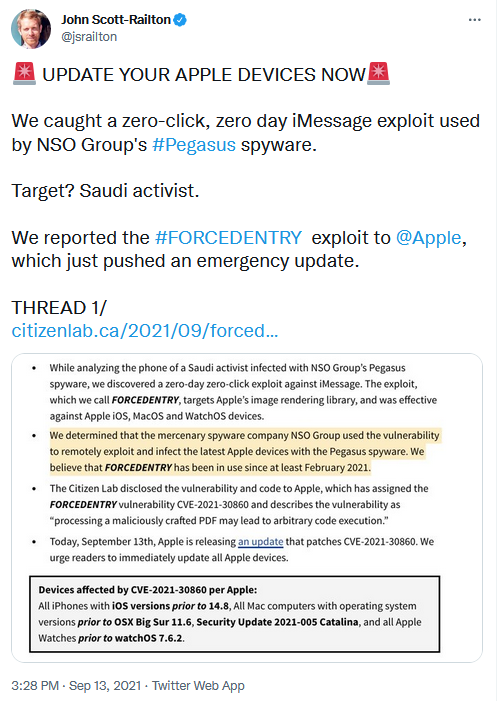
The attack can arrive via iMessage when a maliciously crafted PDF is sent. According to Citizen Lab, which has dubbed the bug ForcedEntry, NSO Group allegedly used the vulnerability to spread a powerful spyware program known as Pegasus, which can secretly take over an iPhone.
A researcher at Citizen Lab discovered the vulnerability while examining an iPhone belonging to an anonymous Saudi activist. The same iPhone contained suspicious GIF files that were actually Adobe PDFs designed to exploit the flaw.
Citizen Lab is warning that NSO Group has likely been using ForcedEntry since at least February to infect the latest Apple devices. NSO Group did not immediately respond to a request for comment. However, the company was most recently accused of targeting 50,000 phone numbers on behalf of its clients.
The second vulnerability, dubbed CVE-2021-30858, only affects iOS, iPadOS and the Safari browser through the WebKit engine. It’ll trigger when the Apple device processes maliciously crafted web content. That suggests attackers have been exploiting the vulnerability by circulating a link to booby-trapped web pages.
Apple has credited that vulnerability’s discovery to an anonymous security researcher. To update your iPhone, go to Settings > General > Software Update. The device can also update automatically if you’ve toggled on automatic updates.
Update: NSO Group didn’t directly comment on Citizen Lab’s findings. The company merely defended its practice of selling spying tools to governments. “NSO Group will continue to provide intelligence and law enforcement agencies around the world with life saving technologies to fight terror and crime,” it said in a statement.
Kan, Michael. “Update Now: Apple Patches iOS, Mac Attack That Uses Malicious PDFs to Hack Devices” PCMagazine September 13, 2021
