
by Stephen Gross | Sep 20, 2023 | Security
Google announced today that it is bringing additional security to the Google Chrome standard Safe Browsing feature by enabling real-time phishing protection for all users. Since 2007, Google Chrome has utilized the Safe Browsing security feature to protect users from...

by Stephen Gross | Sep 20, 2023 | Security
If you’re an IT pro or a serious PC hobbyist, computers are as logical as Mr. Spock. If you’re a human being without a technical background, the average Windows error message might as well be written in Klingon. For that latter audience, computer security...
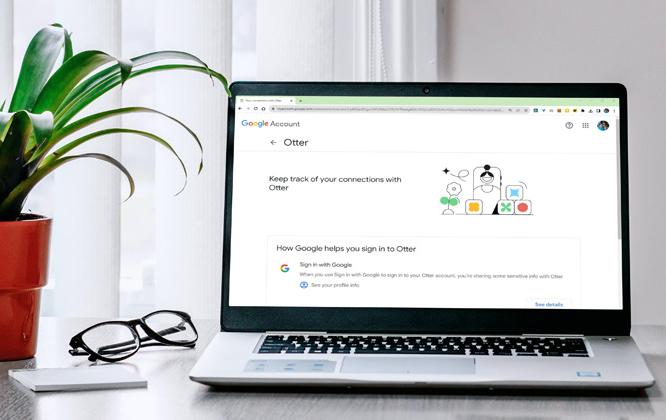
by Stephen Gross | Sep 20, 2023 | Security
What are the risks/drawbacks of logging in with Google? Third-party apps and services are built by external developers and are not owned or operated by Google. So, when you connect them to your Google account, you are granting these apps or services access to use your...
by Stephen Gross | Sep 2, 2023 | Security, Social Media
Your social media posts are a treasure trove of valuable information. Your public contact list alone can help a criminal: The list of names connected to your public social media accounts is enough for a scammer to impersonate a family member or a friend with a spear...

by Stephen Gross | Aug 31, 2023 | Phishing & Awareness Training, Security
Blagging may sound like some complicated hacking technique, but it’s much simpler than that. But while not as “high-tech” as other cyber crimes, blagging can still do serious damage if companies aren’t prepared. So what is blagging and how does...

by Stephen Gross | Aug 29, 2023 | AI, Security
As the public adjusts to trusting artificial intelligence, there also brews a perfect environment for hackers to trap internet users into downloading malware. The latest target is the Google Bard chatbot, which is being used as a decoy for those online to unknowingly...







