
Even though October has been designated as Cybersecurity Awareness month, we strongly encourage you to examine your security protocols every month. Cybercriminals are constantly refining their attack techniques to steal your identity and assets.
Faced with such a range of obstacles, businesses need to change the way they prioritize cybersecurity. The most important step is to put in place several proactive layered security elements to prevent attacks such as:
1. Gateway Firewall with an Anti-Virus and Anti-Malware Suite – to prevent attacks getting into your local network
2. PC and Server Endpoint Protection – to prevent malware
3. Internet Request Filtering Service – to prevent your users from navigating to known malicious websites
4. Operating System and Software Patch Management Plan – to keep your systems secure and updated
5. 2 Factor Authentication (2FA) – to prevent unauthorized access
6. Encrypting Portable Devices – to prevent stolen devices from accessing your information
7. Ability to Remotely Wipe Devices – in the event they are compromised or stolen
8. Dark Web Credential Monitoring – to prevent hackers from using your credentials to access your network and websites you to log into
Cybersecurity is not just using IT solutions, there are also policy, physical security, and user training factors. Consider:
• Physical Security – Limiting access to your offices
• Cyber-safe Policies and Procedures – to govern how employees use technology
• Continuous User Awareness Training – to train users on the latest techniques hackers are using to exploit them.
Even with all of these security protocols in place, phishing attacks are still successful methods of compromising your systems.
LEARN HOW TO SPOT A PHISHING ATTACK
A “QUICK CLICK” can be your worst enemy. When a new email or text message arrives, and it includes something that can be tapped or clicked, our instincts often lead us to a QUICK CLICK too fast. DON’T DO IT!
Hackers have used the pandemic as cover to launch wave after wave of phishing attacks and clever Google Drive scams to get to users while working remotely.
Anyone can fall for these types of scams. The main thing to do is think before you click. Scam messages try to trick people into behaving in a way they normally wouldn’t—with, say, fake instant demands from a boss or messages that convey a sense of urgency.
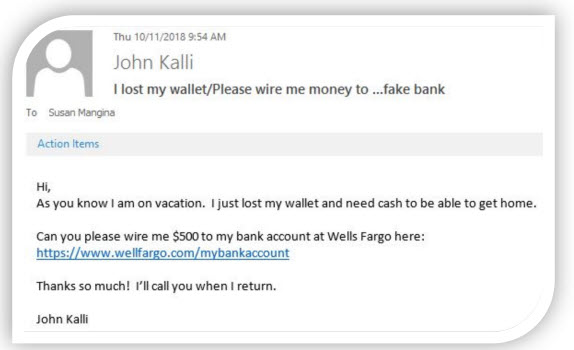
There’s no foolproof way to identify every type of phishing effort or scam. Just like experienced marketers, scammers are constantly upping their game. Just being aware of the techniques that exist can help reduce their effectiveness. Be cautious, think before you click, and download files only from people and sources you know and trust.
Trinity Worldwide Technologies can assist you in implementing these security measures. Please call our office 732.780.8615 or email [email protected].
 John Kalli, CEO
John Kalli, CEO
