
The Emotet malware botnet is taking advantage of the 2022 U.S. tax season by sending out malicious emails pretending to be the Internal Revenue Service sending tax forms or federal returns.
Emotet is a malware infection distributed through phishing emails with attached Word or Excel documents containing malicious macros. Once these documents are opened, they will trick the user into enabling macros that will download the Emotet malware onto the computer.
Once Emotet is installed, the malware will steal victims’ emails to use in future reply-chain attacks, send further spam emails, and ultimately install other malware that could lead to a Conti ransomware attack on the compromised network.
Emotet impersonates IRS.gov
In a new report by email security firm Cofense, researchers have spotted multiple phishing campaigns impersonating the Internet Revenue Service (IRS.gov) that use lures related to the 2022 U.S. tax season.
These emails pretend to be the IRS sending the recipient their 2021 Tax Return, W-9 forms, and other tax documents commonly required for the tax season.
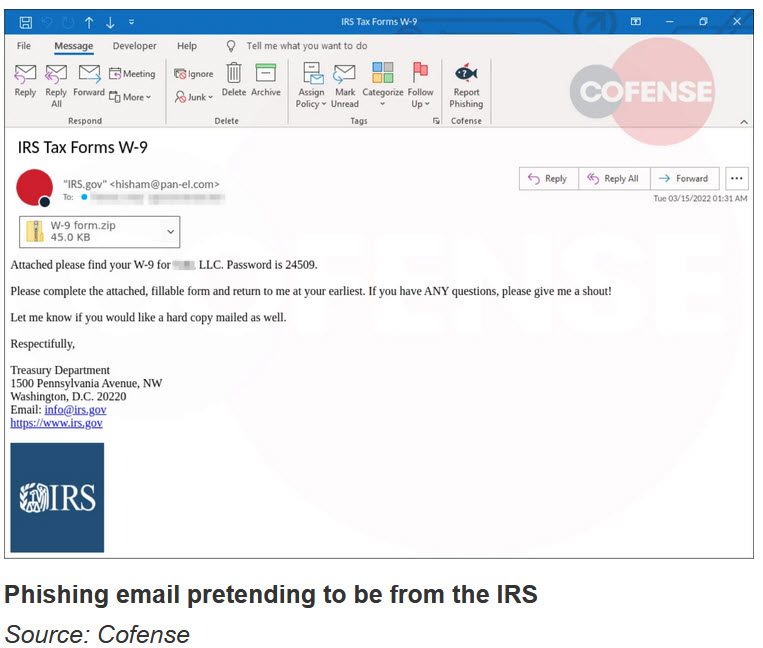
While the email subjects and text of the IRS-themed emails vary, the general lure is that the IRS is contacting your business with either completed tax forms or ones you need to fill out and return to them.
An example of the text found in one of these emails is:
Attached please find your W-9 for [company_name] LLC. Password is 24509.
Please complete the attached, fillable form and return to me at your earliest. If you have ANY questions, please give me a shout!
Let me know if you would like a hard copy email as well.
According to Cofense’s report published today, the phishing campaign is using numerous email subjects related to the U.S. tax season, including:
IRS Tax Forms W-9
Incorrect Form Selection
INCOME TAX RETURN 2021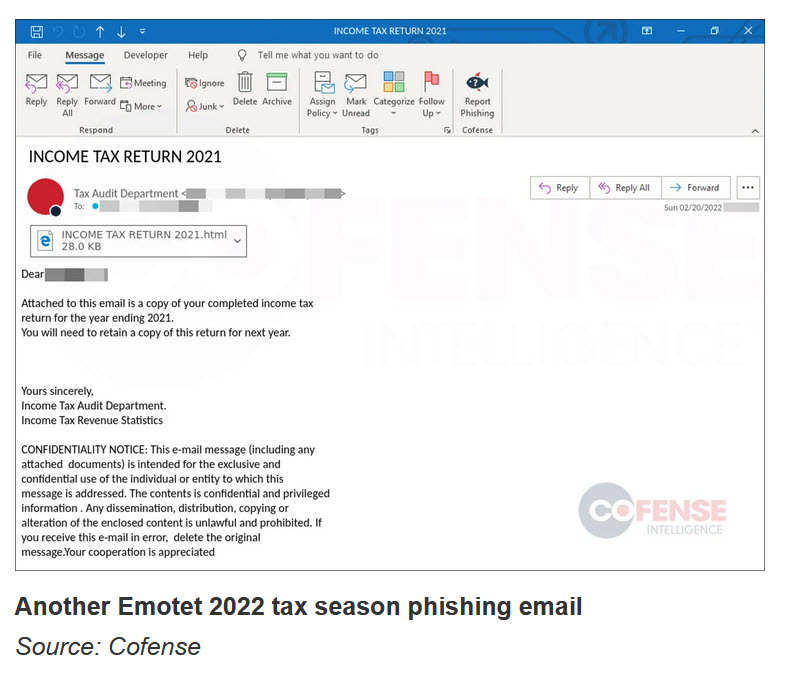
Attached to the emails are zip files or HTML files that lead to zip files, which are password-protected to make it harder to detect by secure email gateways.
In tests conducted by BleepingComputer, these zip files fail to be parsed correctly by Windows’ built-in archive extractor, potentially causing the campaign to have less impact.
However, third-party archive programs, like 7-Zip, have no problem extracting the files, as seen below.
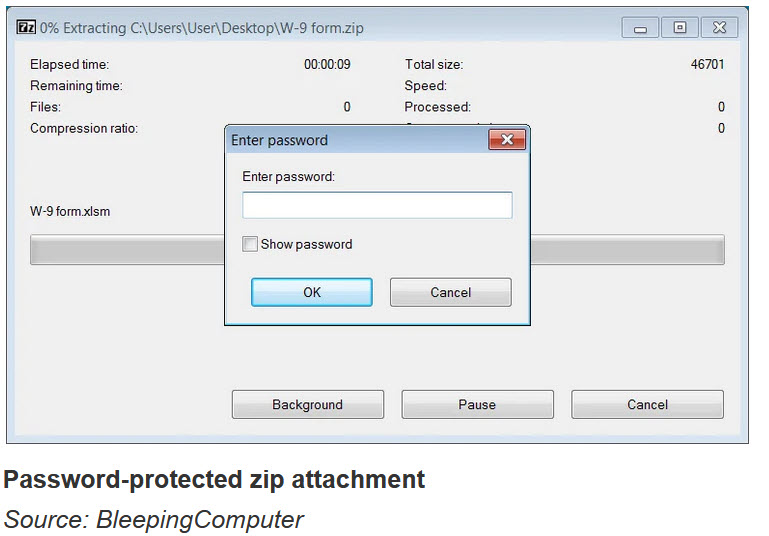
Inside the zip files is a ‘W-9 form.xslm’ Excel file that, when opened, prompt the user to click on the “Enable Editing” and “Enable Content” button to view the document correctly.
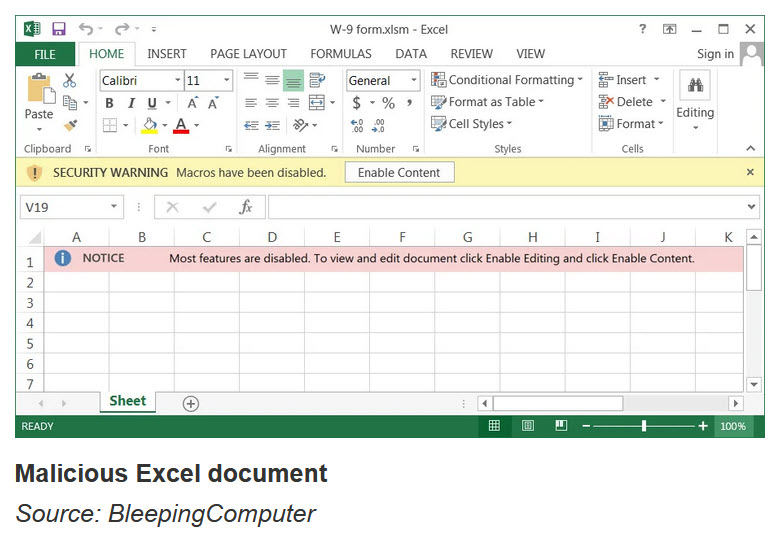
Once a user clicks on these buttons, malicious macros will be executed that download and install the Emotet malware from hacked WordPress sites.
Once Emotet is installed, the malware will download additional payloads, which have commonly been Cobalt Strike in recent campaigns.
However, the Emotet research group Cryptolaemus has also seen Emotet dropping the SystemBC remote access Trojan.
With Emotet now developed by the Conti Ransomware gang, all organizations, large and small, should be on the lookout for these phishing campaigns as they ultimately lead to ransomware attacks and data exfiltration.
As always, it is vital to remember that the IRS never sends unsolicited emails and corresponds only through the postal service. Therefore, if you receive an email claiming to be from the IRS, mark it as spam, and delete the email.
